User Scenarios | IoT
Greater storage capacity for your IoT environments thanks to cloud infrastructure

IoT environments, at the forefront of technology
Connecting different devices and sharing information has become a technological necessity that is increasingly demanded by both businesses and individual users. And this forms the basis of IoT infrastructure or the Internet of Things, which is a network of devices and objects connected to the Internet. It is precisely these objects that set the IoT apart from the traditional network, as they can be anything from sensors, home automation tools and industrial actuators to everyday objects such as watches, refrigerators or even shoes and clothes.
There are many examples, both in everyday life and in business, where the IoT is becoming increasingly important:
- Domotics allow a home to be automated and connected remotely, using data collected by sensors to control connected equipment (thermostats, smart lights, surveillance cameras and all other supported appliances) from anywhere.
- The industrial sector, Industrial Internet of Things (IIoT). In this case, production plants can be controlled and monitored remotely and, depending on the data obtained, can even initiate automatic action protocols based on alert thresholds without the need for human interaction. For example, by controlling the pressure of steam circuits which automatically act on the exhaust valves in the event of excessive pressure.
IoT Environment Solutions
The basic pillars of an IoT architecture are having an external platform where the obtained data can be stored, analysing that data, and keeping access to it as simple as possible.
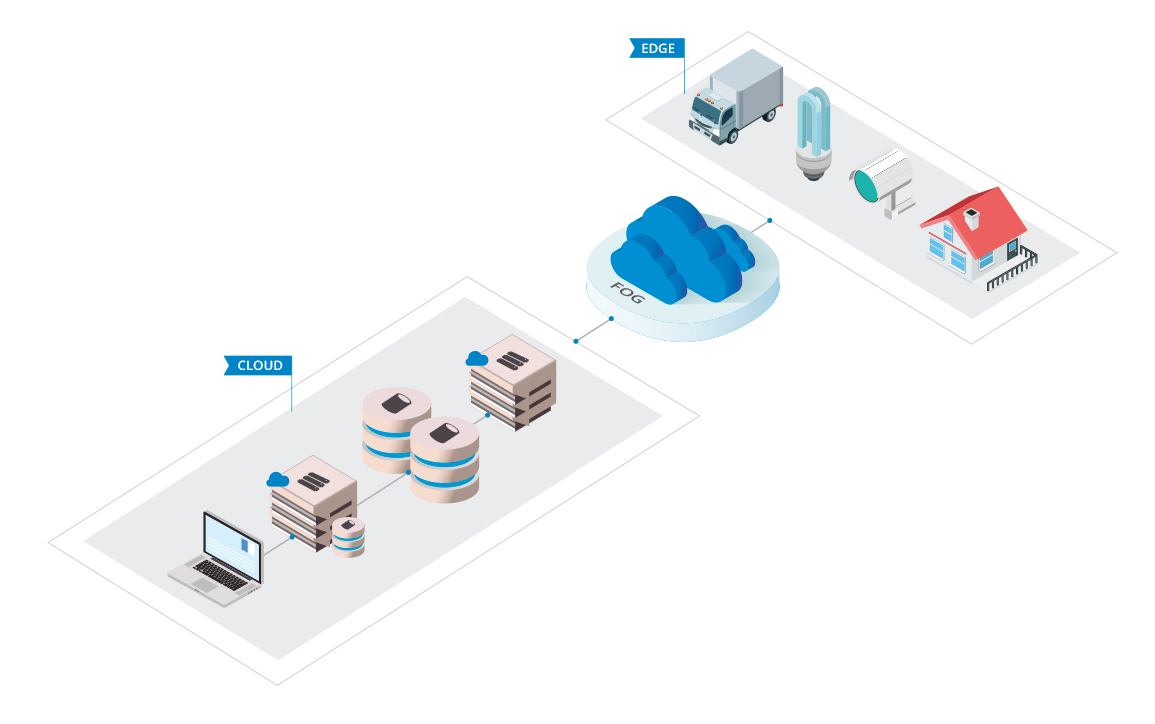
To create your IoT environment in the cloud, we will accompany you from design to implementation and subsequent operation. To design your solution we will take into account your processing and storage needs, as well as your requirements when making decisions based on collected data. Using this information, we will suggest the most suitable service. This may not always be a complete cloud solution as sometimes a real-time response to specific data may be required, as the process must be carried out closer to the origin. This has come to be called EDGE Computing.
Due to the variety of protocols used in the IoT today and the different possibilities when deploying a solution of this type, we offer a platform that is neutral to any protocol and as standard as possible so that you can easily adapt it to your needs.
One of the main characteristics of the IoT is the large volume of data required for storage. There are generally two types:
- Large files (such as security camera videos, sound recordings, etc.) that do not require immediate processing and can be stored neatly for later reference.
- Smaller databases that are mostly text-based but with large I/O requirements fed by IoT device sensors. This data does require immediate processing and their consultation and modification requires a great deal of computing power.
Once these databases are deployed, our cloud solution allows you to increase the resources of the platform automatically should it detect a massive consumption of resources in your servers or the traffic that is being generated from your IoT devices. At Arsys, thanks to the exhaustive monitoring of the platforms hosted in our systems, we are able to adapt your solution according to your needs, whether it means increasing resources or deploying hybrid platforms.
In addition, we will provide you with everything you need to host your Business Intelligence and Machine Learning tool. This way, you will get the most out of your data because being able to access it, process it and make decisions is even better than having it, In this aspect, we will help you to deploy tools such as Microsoft Power BI or Tableau or other opensource tools such as Grafana or ELK in distributed platforms, in HA and completely securely, allowing you to optimise the use of Big Data in your business.
All our IoT solutions are designed and operated under the strictest safety regulations. For us, this is a priority and a point of improvement for many of the IoT solutions on the market. The IoT platform we design for you will include data security tools, with data encryption and periodic backups. You will also have access to security in the communication channel, with the possibility of deploying VPN, point-to-point lines or MPLS to ensure the safe transit of data from origin to storage.