Managed security, vulnerability management and malicious code control services

We can help you prevent threats with our Managed Security services
It is increasingly common to experience attacks and malicious activity on the Internet. That's why it is essential to determine both the possible threats and the way to mitigate them. We offer several Managed Security services to help you avoid and mitigate possible threats such as:
- Systems infected by viruses, worms, Trojans or spyware
- Theft of an organisation's identity in order to obtain confidential data
- Attempts to saturate systems so as to degrade or interrupt a service
- Fraudulent electronic transactions
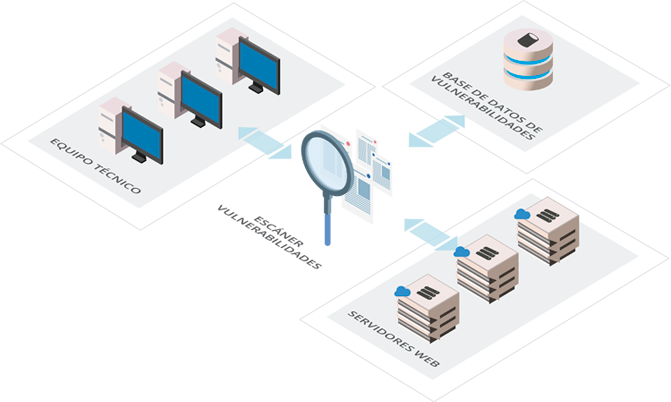
Vulnerability Management
One of the main concerns of an administrator when installing a server is to ensure that everything is correctly configured and updated and that it remains secure over time.
To facilitate this task, we offer a Vulnerability Management service that provides fast, accurate and complete information about the vulnerabilities of your server. It also ranks vulnerabilities and potential risks so you can prioritise them in order of criticality. Finally, it facilitates prevention as it has a continuous 24/7 automatic update against the technology manufacturer's research centre. This is how we help your system administrator to be prepared for threats.
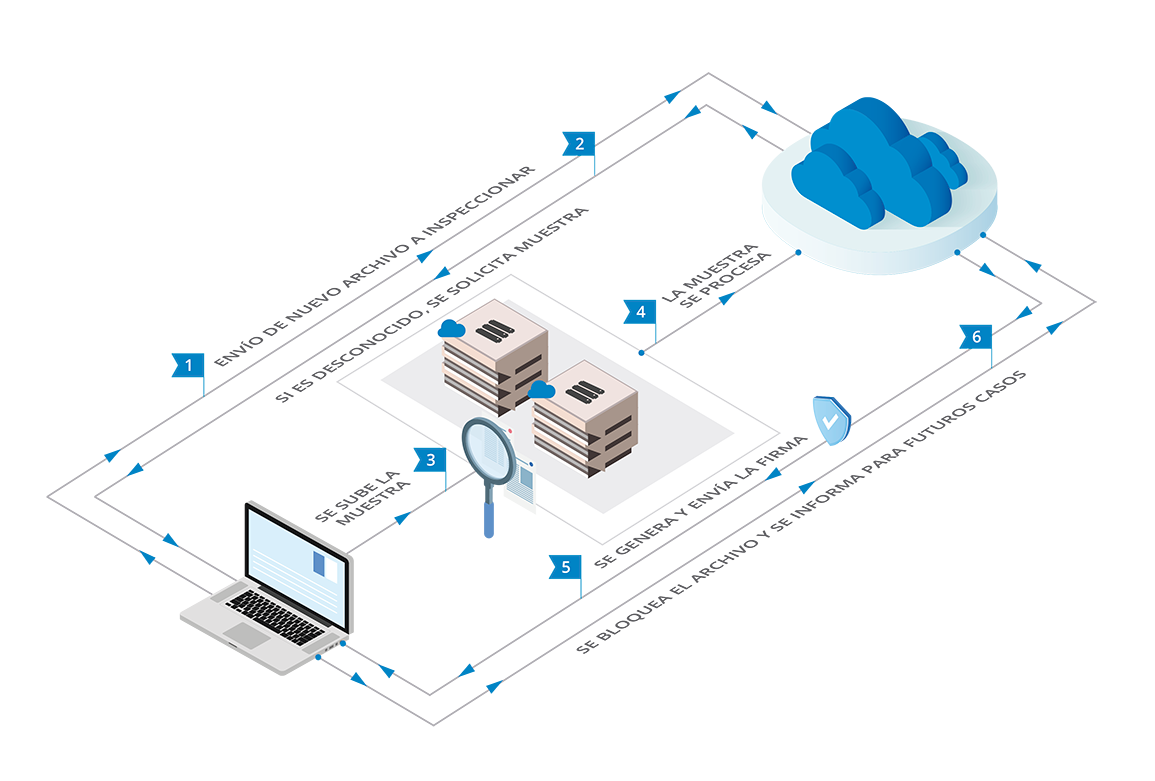
Malicious Code management
The huge daily volume of malware or malicious code threats that can affect the servers that serve your end users forces the system administrator to implement and manage a protection tool.
Our Malicious Code Control service detects and cleans malware, minimising its impact on the performance of your servers. It combines different technologies to protect server systems and files from threats such as viruses, spyware, bots, worms, Trojans, buffer overflow attacks (targeting Microsoft application vulnerabilities) and blended attacks. You won't have to worry about a thing because our technical staff will manage:
- The most appropriate security policies to meet all your requirements: folders and files to be scanned, real-time or scheduled scanning, etc.
- The generated alerts from the administration console.
- Malware removal whenever possible, and, when it is not, the execution of previously agreed actions, such as quarantining the file, denying access to it, deleting the file, etc.